Configure the firewall settings for your MongoDB SSL connection
Configure your firewall settings for a secure MongoDB SSL connection.
For a secure network configuration, the Sitecore xDB Cloud service uses a MongoDB SSL connection.
To configure your firewall and application servers for use with MongoDB SSL connection as part of Sitecore xDB Cloud service, you must:
Open the firewall ports for hostnames and ports listed for the MongoDB connection strings you receive from Sitecore. For example, the following MongoDB URI,
mongodb://<dbuser>:<dbpassword>@*-a0.*.fleet.mongolab.com:0000,0000.*.fleet.mongolab.com:0000/<dbname>?replicaSet=rs-0000&ssl=true
contains the following hostnames and ports:
**0000-a0.***44.fleet.mongolab.com, port 0000
046408-a1.44.fleet.mongolab.com, port 0000
Connect to your MongoDB server using HTTPS, for example, https:// 0000-a0. 0000.fleet.mongolab.com:0000, and download an SSL certificate for your MongoDB database.
MongoDB responds with the message: It looks like you are trying to access MongoDB over HTTP on the native driver port.
Click the padlock icon to review your connections in the Certificate Viewer.
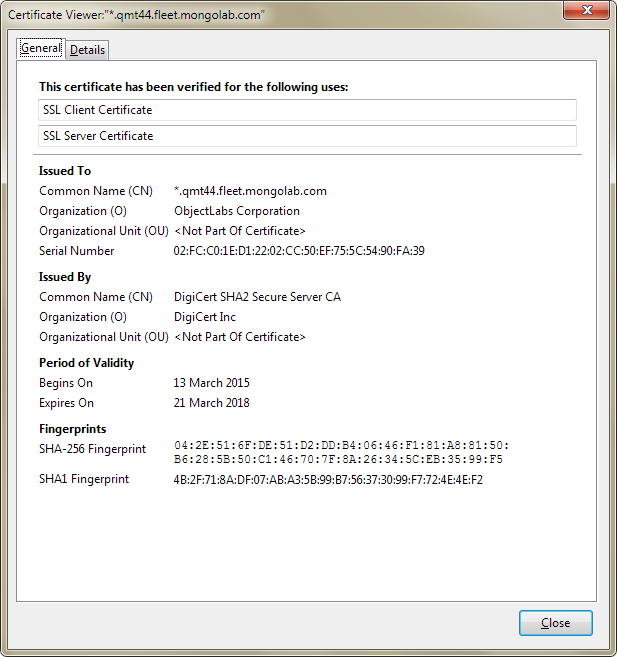
Download and install the Trusted Root Authority certificate to the application server that is running Sitecore.
In the Certificate Viewer dialog, on the Details tab, in the Certificate Fields field, click Authority Information Access. It contains a link to the certification authority certificate CA Issuers: URI, that you can copy and paste into your browser, for example:
http://cacerts.digicert.com/DigiCertSHA2SecureServerCA.crt
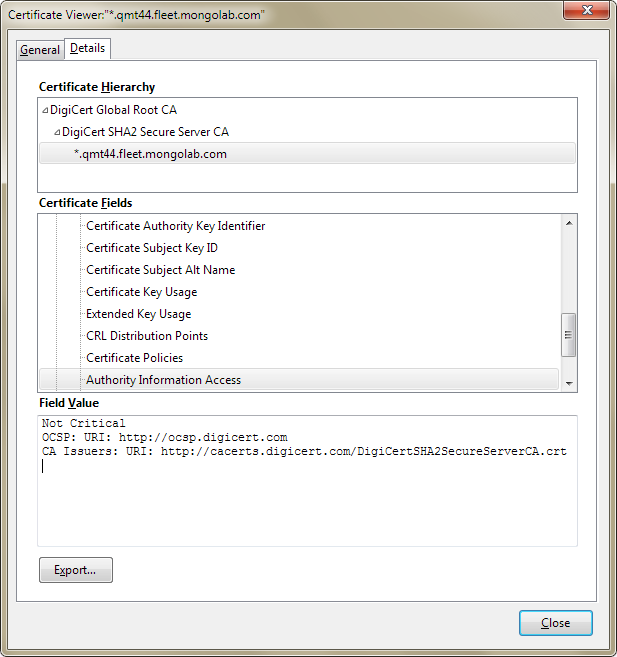
Download the
.crtfile to the application server, then install into (Local Computer)\Trusted Root Certification Authorities\Certificates certificate store. You can read more about adding Trusted Root Certification Authority certificates on the Microsoft website.In your firewall, go to the On-line Certificate Status Protocol endpoint for Digicert, ocsp.digicert.com, and open access to port 80.
To open access to the Certificate Revocation Lists (CRL) Distribution Points, in your firewall, open the Certificate Viewer dialog. On the Details tab, in the Certificate Fields field, click CRL Distribution Points.
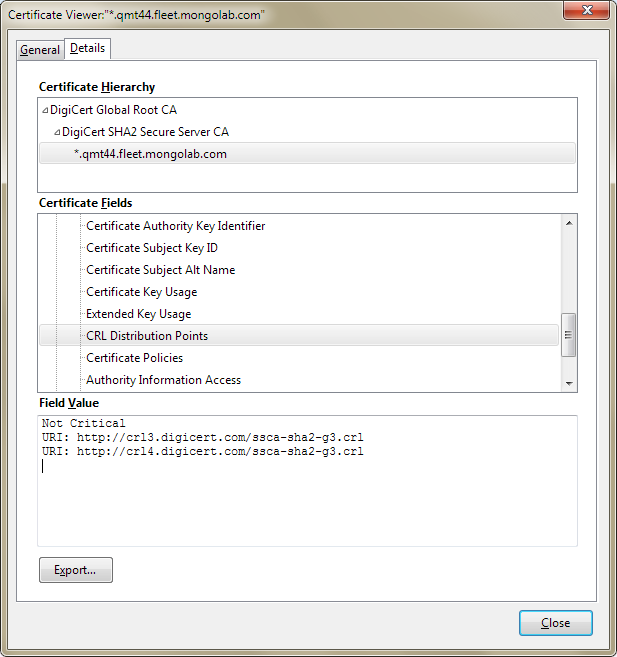
Note
You can use the DigiCert Certificate Utility to verify server access to CRL and OCSP endpoints.